 |
| New job offer link with malicious code on linkedin |
LinkedIn, the largest networking professional networking, is is where more than half of all phishing activities in the world take place, according to research by checkpoint. Phishing is the practice where an attacker manipulates and misleads a recipient into giving up privileged information or access to corporate systems.
Criminals love phishing for victims on social media networks more than attacking other industries like shipping and retail. While LinkedIn tops the 2022 list as most targeted list, Whatsapp and telegram are not far behind which used for delivering scams in Africa.
Of course, what better way to gain such privileged access than to lay traps on a network of over 830 million members holding all sorts positions in private, non-profit and government enterprises. In short, this is the ideal network to actively participate on, if you are looking for job and/or want to continually bombard your work friends with each new shiny certificate/job/award you achieve.
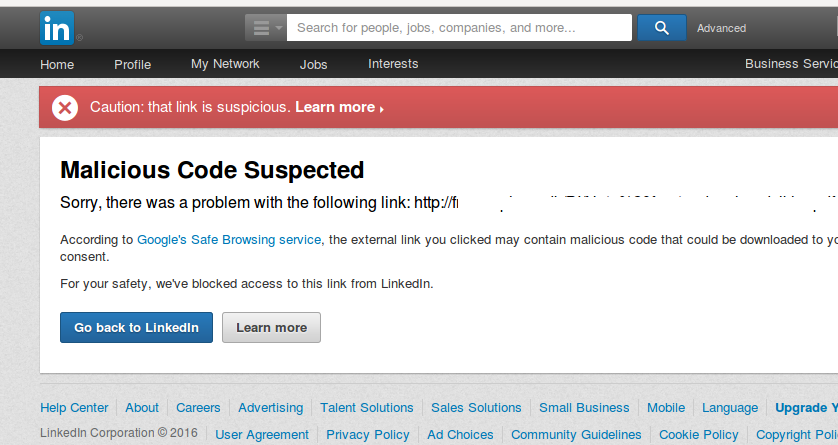
A few years back while job-hunting, i clicked on a malicious link (screenshot above) that was luckily detected and categorized LinkedIn as such. Thereafter i reported it to the recruiter who was surprised to find out that the job description page was hacked and infested with malicious code.
Once the cyber criminals gain access to corporate systems, they listen in on the communications taking place with aim of locating the individuals with the "keys to the kingdom" (administrator access). When administrator credentials are stolen, the criminals then proceed to steal all critical data to the business and thereafter activate ransomware thus crippling the entire business.
A few pointers to reduce instances of spilling personal or critical information to unauthorized individuals:
- When you get a job link, type it into browser instead of clicking it. Type in the domain part - for instance, BYG.yy and navigate to the job description posted somewhere on the website, possibly under "careers" section.
- As an organization, consider offering periodic cyber awareness and training sessions to staff, clients and partners highlighting the changing tricks of cyber criminals. Training can cover how to spot misspelled website names, shortened links and passwords management.
Comments
Post a Comment